OT industrial cybersecurity: Hardening the ModBus protocol
Learn how to find and protect IoT devices on the Internet
OT stands for Operational Technology, contrary to the IT that is Information Technology. Inside IT we put things such as servers, computers, laptops, smartphones, etc. OT is more focused on more low-level devices that keep factory lines busy, as for instance, a PLC (Programmable Logic Controller) that can control an hydraulic valve or a nuclear plant valve.
One of the most used industrial protocols is ModBus protocol. Contrary to many other propietary protocols, ModBus uses TCP/IP for communications.
Usually ModBus connections use TCP/502 port, however this port is unsecure by default as communications are not encrypted AND any attacker can impersonate a master device to perform unexpected actions.
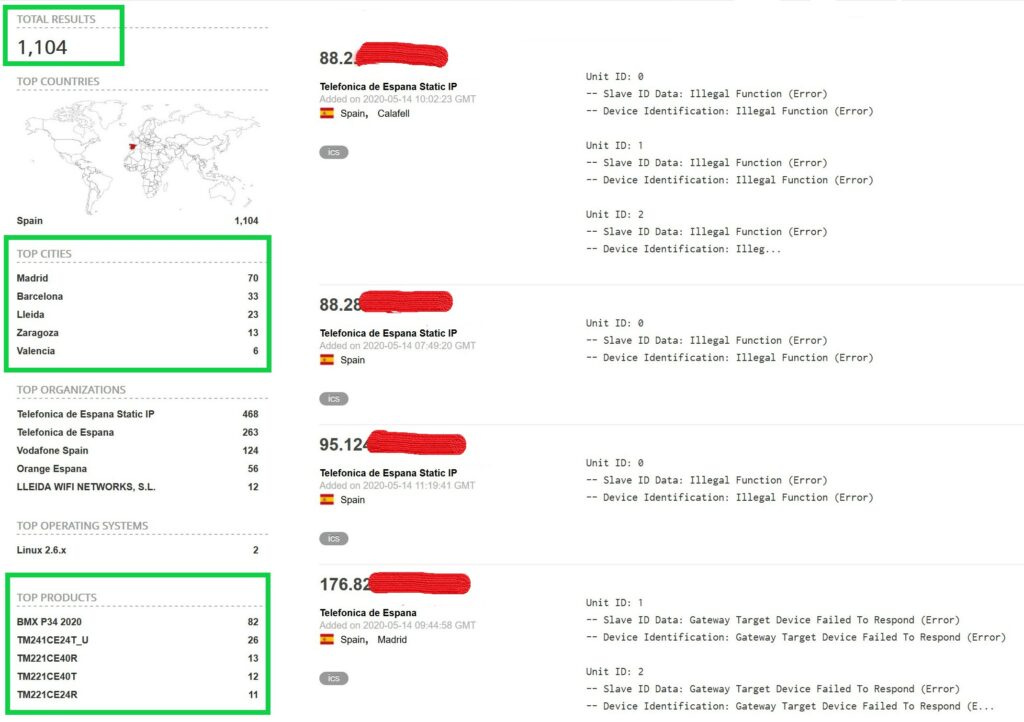
Guess how many openly available ModBus devices are public on the Internet:
So, first thing to keep in mind is: NEVER expose industrial devices to the Internet if you do not plan that some attacker literally hacks your factory.
Second thing, upgrade your protocol and use TCP/802 instead of default TCP/502 as the first provides encryption.