Interactsh: Open-Source OOB solution for SSRF, Blind SQLi, ... in Kali Linux
Project Discovery, the same people behind Nuclei scanner that allows you to customize vulnerability scanning from YAML templates, just released another awesome project called Interactsh.
To keep it quick and short, it's a free alternative to Burpsuite Collaborator for free that you can use in their SaaS platform or just deploy it in your own server.
OOB attacks, or Out-of-Band attacks, are blind injections in which we can send a URL to connect back to our server from the target infrastructure to know if it is vulnerable or not. Three of the most common OOB vulnerabilities are SSRF (Server Side Request Forgery), blind stored XSS and blind SQL injection.
First you will have to install Go, if you haven't already:
sudo apt install golang-goThen we can install Interactsh directly from the official github repository in our home directory:
cd
GO111MODULE=on go get -v github.com/projectdiscovery/interactsh/cmd/interactsh-clientReady! Now you can easily run the tool and set up a OOB environment in milliseconds:
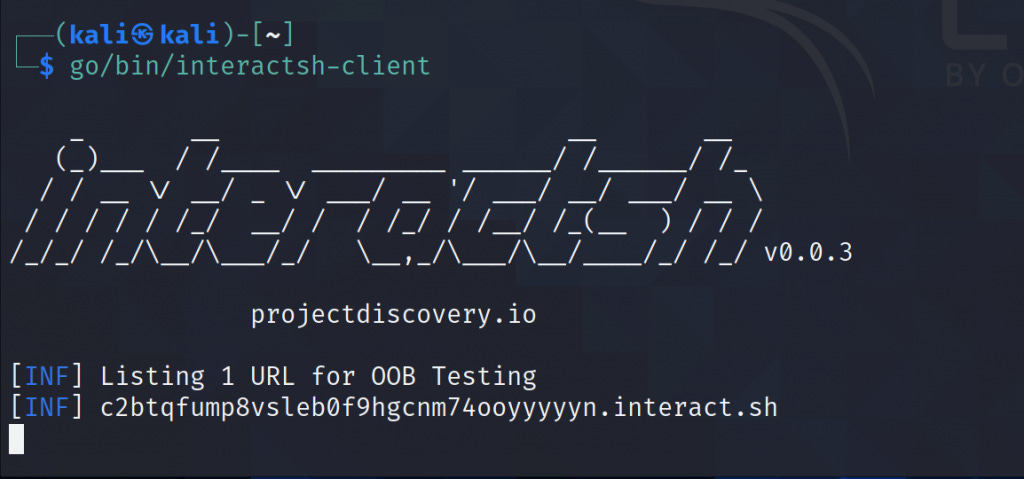
go/bin/interactsh-clientIn this example, you can use the above URL ("c2btqfump8vsleb0f9hgcnm74ooyyyyyn.interact.sh") to use it in your payloads and validate if a website is vulnerable to any type of blind injections such as SSRF, Blind SQLi, etc.
Keep in mind that this URL is a wildcard, we can add any subdomain in front of the interactsh URL and we still get the connection back. You can use either http:// or https:// protocols when the client does not validate the server certificate.
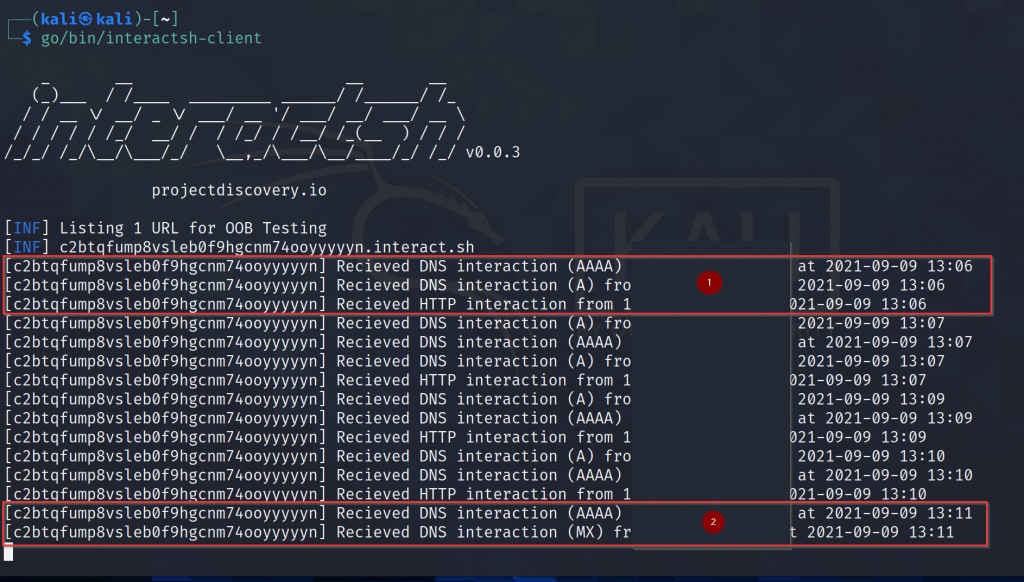
You can expect some output like in (1), when there is a successful HTTP(s) connection back, or like (2) when the vulnerable program only does a DNS resolution. In either way, you can easily prove that there is an OOB vulnerability.
You might be also interested in:
Happy hunting!