Sometimes when doing lateral movement in a penetration testing engagement, we don't want to use nmap to keep a low footprint. There it comes netcat to the rescue which it is already installed in many Linux systems.
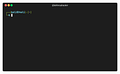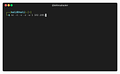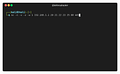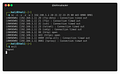
With this command we can easily perform a port scanning for the most used ports:
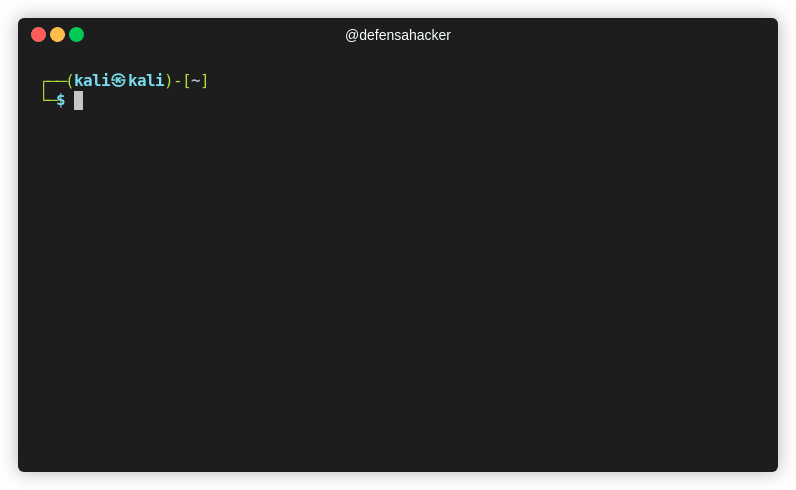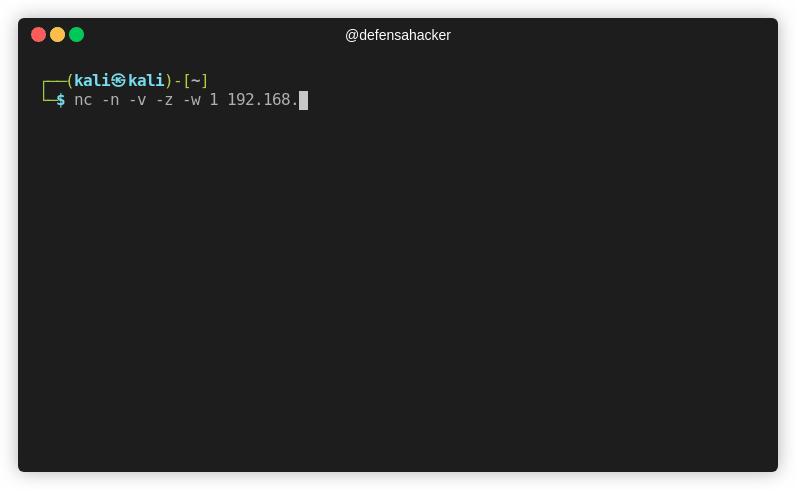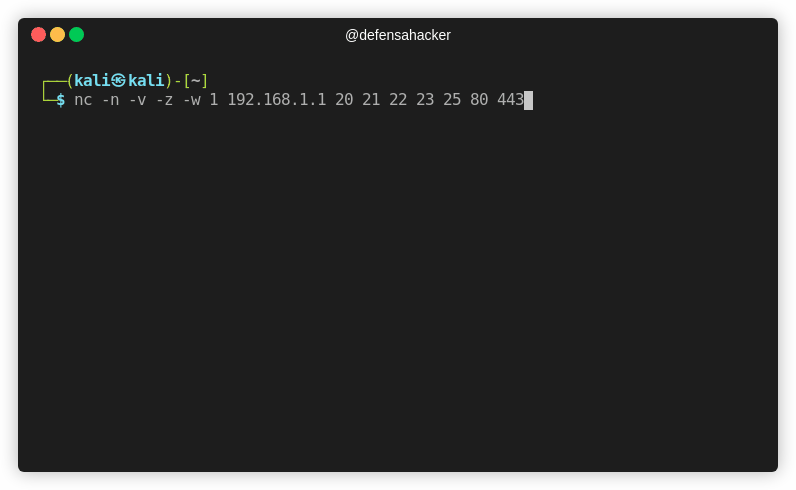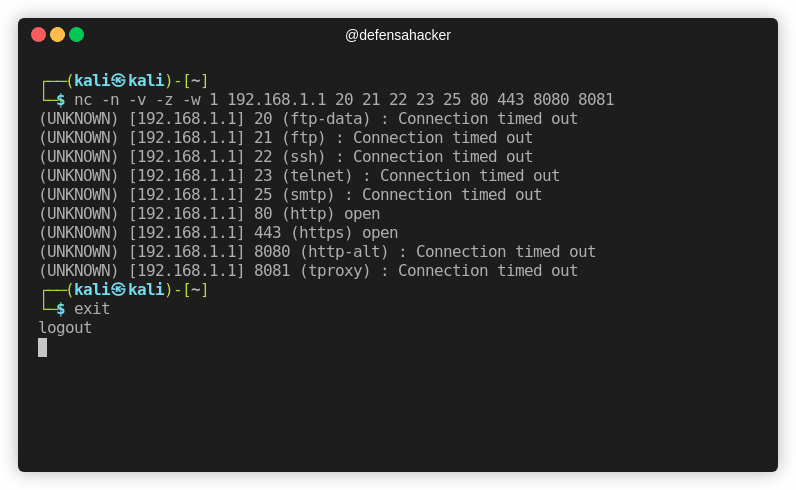
nc -n -v -z -w 1 192.168.1.1 20 21 22 23 25 80 443 8080 8081If you are willing to scan all 65535 TCP ports, take your time, it takes around 1 second per port as specified with -w 1 flag:
More tricks in the Enumeration penetration testing post: